Email phishing scams are more than an annoyance. They’re an epidemic.
Phishing attempts increased by 65% in 2017 — and nearly 1.5 million new phishing sites pop up every month.
Today we’re tackling everything you need to know about phishing, including:
- The definition of phishing
- Types of phishing
- Phishing email examples
- How to spot phishing emails
What is Phishing?
Chances are you’ve encountered spam or phishing emails. It’s when criminals pose as legitimate companies and institutions online to lure individuals into providing sensitive information including banking, credit card and password information.
Phishing emails come in various forms. It might be a familiar company or service, asking for your password.
Or, it’s from someone you know, but it seems just slightly off.
For example, say you get an email from your boss asking you to pay an invoice that looks unfamiliar. Or, your coworker asks you to make an unusual purchase with the company credit card that seems entirely out of the blue.
Phishing can also come in the form of spammy links or attachments that install malware on your device when you open it.
Types of Phishing Emails
There are two main types of phishing emails; clone phishing and spear phishing.
Clone Phishing
Clone phishing is when hackers create malicious, almost identical copies of legitimate emails from reputable sources to trick targets into unknowingly sharing their information.
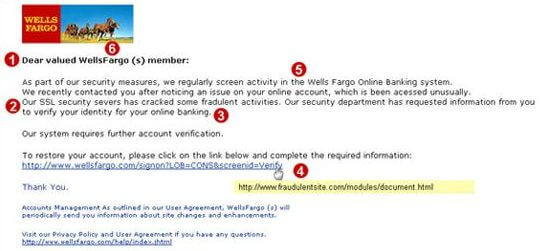
Here’s an example of a clone phishing email:
There are a few signs that indicate this is a phishing email:
- It’s not addressed directly to you
- There aren’t any personal tells or identifying markers in the email
- It has spelling and grammar errors (they help bypass email filters)
- Misspells the company name
- Urges immediate action
If you were to hover over the link (don’t click it), you’d probably see a link that takes you somewhere other than WellsFargo.com.
Don’t click the links if you’re unsure of the source. If it asks for your login information, exit the email and go directly to the site in your browser to log in.
Spear Phishing
Spear phishing is a little trickier and more difficult to detect. Instead of copying legitimate emails, spear phishing involves targeted attacks aimed at specific individuals or companies.
In spear phishing, cybercriminals carefully research your online fingerprint. They observe the websites you visit and your social media profiles to identify where you shop, recent purchases, the companies you like, where you work and who your family and friends are.
They use personal details to disguise themselves as a trustworthy source.
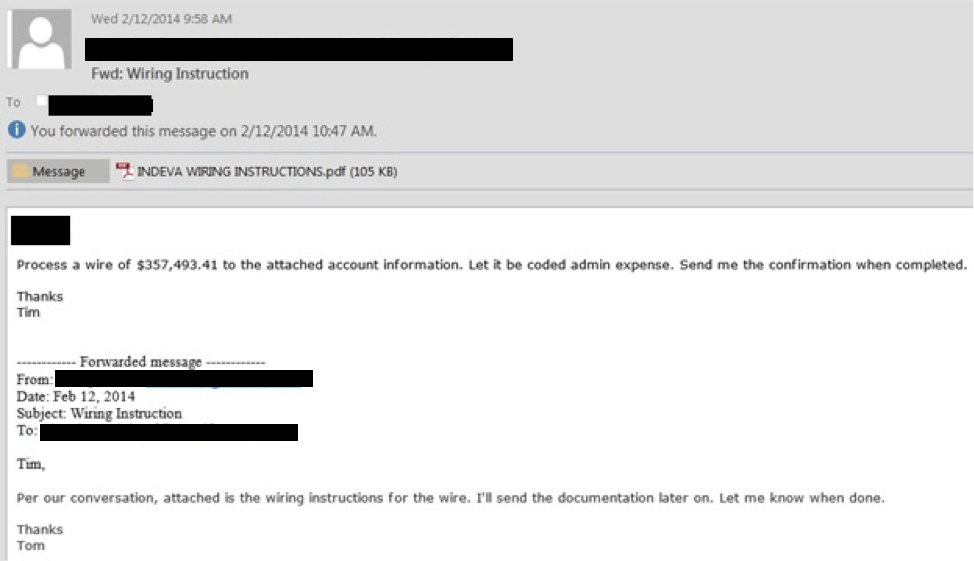
Here’s an example of a spear phishing email:
Here are a few indicators:
- It’s directed to a specific individual
- There aren’t any spelling or grammar errors
- It urges immediate action
Spear phishing mails often have login links and attachments like the example above. If you click the link, it takes you to a copycat version of your standard portal — the URL of the portal will be slightly different from your usual one.
However, if you’re rushing through a busy day answering emails, these are easy details to miss.
How to Spot Phishing Scams
The best defense in phishing is education — knowing what to look for and what to do if you encounter a phishing scam.
Phishing scams are highly customized. It’s difficult to spot phishing emails, especially during a busy day.
Here are a few things to look out for:
- Check spelling and grammar
- Make sure the links are safe (if you’re not sure, log in through your web browser)
- Pay attention to file extensions and attachments
- Look at the email address
- Ensure everything is specific and the sender can prove their identity
What to Do When You Spot a Phishing Email
Here are some best practices to follow when you receive a suspicious looking email
- Don’t clink any images or links
- Don’t give any personal information
- Don’t click on or open any attachments
- Delete, delete, delete if you are at all suspicious
- Report it to your IT admin
Bulk Up Your Defenses With Helixstorm’s Managed IT Services
At Helixstorm, we’ll help you partner on every technical aspect of your business. From support desk help to IT strategy and planning, we’ll assess your network and help you secure and optimize your IT environment at every level of your business.
Interested? Contact us today for a free network assessment.
Related

Aaron Schneider is the President of Helixstorm, bringing over 20 years of experience in the technology industry. Specializing in cloud computing, business continuity, virtualization, and business technology planning, he helps businesses integrate and adapt new technologies for seamless systems.